The 5 a.m. Crisis: Navigating the High-Stakes Tug-of-War of Mobile Discovery
By Warren Kruse
February 20, 2026

Warren Kruse is the Managing Director at iDiscovery Solutions (iDS). A former New Jersey police officer, he has worked at government agencies and global corporations and led billion-dollar cross-border investigations. Kruse has unraveled intellectual property theft, exposed fraud, and guided organizations through the pressure of regulatory scrutiny. He can be reached at wkruse@idsinc.com.
The 5 a.m. glow of a smartphone screen is never the harbinger of good news for a general counsel. As the vibrating mobile dances across the nightstand, you grab the device and answer.
“We have a problem,” says the voice on the other end. “On the investigation there’s a specific thread of messages detailing the allegations and it’s all on the custodian’s personal device.”
Suddenly, the GC is caught in a high-stakes tug-of-war of mobile discovery, balancing privacy, preservation, and legal exposure. As the sun begins to rise, the corporate counsel must decide: Do we “grab” the mobile for the data to satisfy the court, or move cautiously and risk the evidence vanishing into the ether—along with the case?
This scenario is happening more and more. In today’s high-tech world, critical evidence lives on personal smartphones, inside messaging apps, cloud backups, and ephemeral platforms that were never designed for litigation.
“The use of mobile devices is ubiquitous. As a result, it is not surprising that they are an increasingly relevant data source in litigation,” the Sedona Conference wrote in its May 2025 “Commentary on Discovery of Mobile Device Data.”
Demanding a forensic image of a personal device is a trial in itself. I’ve seen forensic imaging from every angle: law enforcement, corporate security, and consulting. In law enforcement, you legally seize the device. In the corporate world, we needed to balance business needs. As an expert, the role shifts to one of defensibility, proportionality and precision.
Even the most cooperative custodian may hesitate to surrender their device, not necessarily for illicit reasons, but because the device is deeply personal and essential to daily life.
This creates a high-stakes balancing act for any legal department:
- The custodian’s device holds the key to the investigation. They may not want to give up the device. They may have commingled data.
- The volatility of data: mobile data is ephemeral. Encryption, auto-delete timers and remote-wipe capabilities mean that the window for defensible preservation is measured in minutes, not days.
- The shadow of spoliation: We sometimes hear “it is on a private device, not a corporate system, but if business was conducted there, the burden of preservation rests on the company,” says Aaron Crews, Partner Holland & Knight.
With that context in mind, consider the hypothetical scenario of the custodian’s personal device described above. From there, you can develop a defensible mobile discovery strategy that protects the custodian’s privacy without compromising the integrity of the investigation. We’ll review the tools counsel should consider using—but before jumping into collection, it’s critical to first evaluate the matter, define the needs, and appropriately scope the effort. Every matter is unique.
Phase 1: The nature of the allegation
Are we looking for intent, communication patterns, or specific files? Don’t forget a mobile device isn’t just pictures, email and texts. It can contain files.
Phase 2: Surgical scoping
Is the device corporate-owned (COPE) or bring your own device (BYOD)? This distinction is the legal fulcrum upon which your authority to collect rests.
Dennis Russell Kiker, Senior Attorney at DLA Piper, advises: “I would recommend that the client document everything we know about the custodian, the device, and the ‘key evidence’ believed to be on the device, while simultaneously retaining a qualified forensic analyst for guidance and collections support.”
I didn’t even ask him to add the last part, but it perfectly captures the reality that good investigations are as much about process and expertise as they are about data.
High-level scoping principles:
- What is needed from the device and what app was used is just as important as what type of device is involved.
- Define the “relevant period.”
- Identify parties to include or exclude.
- Identifying where original data might live outside the physical handset
Ryan Bosselman, Chief Operating Officer at ModeOne Technologies, offers this insight: “When custodians know that only relevant data will be collected, and personal content explicitly excluded, cooperation increases and risk decreases. That’s what privacy-centric mobile discovery looks like in practice.”
At this stage, we want to go into our tool bag and select the best tool for the job. The tool that allows counsel to execute the scope they’ve defined, whether that means preserving an entire device or isolating a single conversation.
Phase 3: What a defensible collection actually looks like
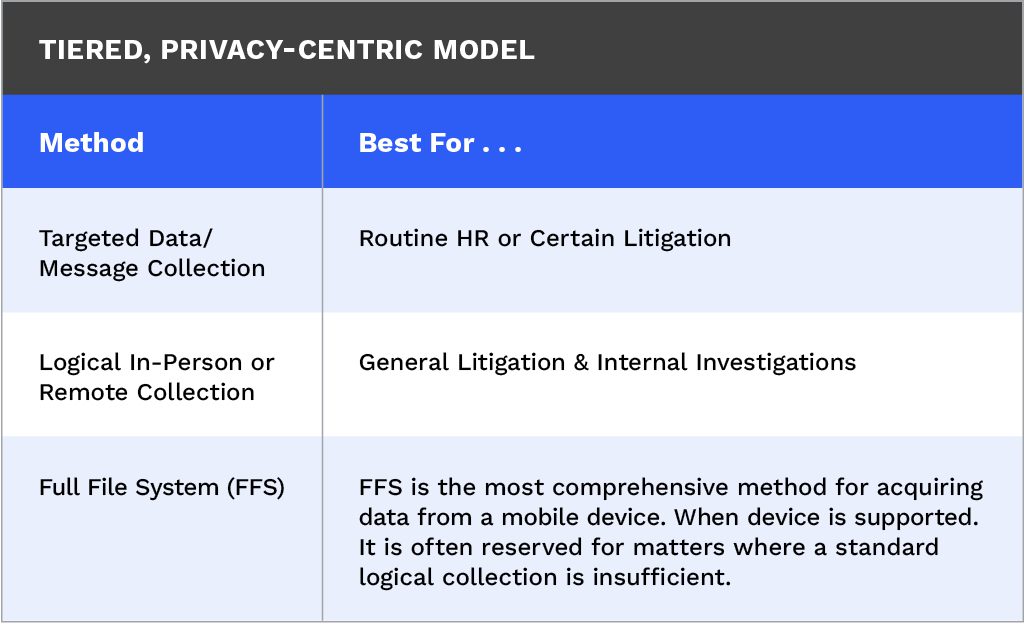
Mobile data collection follows a tiered approach, guided by the needs of the matter and technological advancements—such as the ability to remotely target mobile data or to preserve data first and then apply advanced filtering to isolate what is needed.
Logical in-person or remote collection is typically used when a complete logical snapshot of a device is required. In contrast, targeted data or message collection is best suited when:
- The scope is narrow and well documented
- The objective is to preserve specific data rather than conduct a deep forensic examination
Conclusion
Mobile collection should not be considered a “one-size-fits-all” forensic exercise. For corporate counsel, the focus has shifted from mere data acquisition to defensible, risk-adjusted strategies that prioritize proportionality and privacy.
This requires a careful balance to avoid the twin hazards of over-collection or under-preservation of mobile communications.
Must read intelligence for general counsel
Subscribe to the Daily Updates newsletter to be at the forefront of best practices and the latest legal news.
Daily Updates
Sign up for our free daily newsletter for the latest news and business legal developments.